
3 Ways Anomaly Detection Enhances Network Monitoring
With the increasing abstraction of IT services beyond the traditional server room computing environments have
It’s what you don’t see that poses the biggest threats and invisible dangers and you need real visibility to know what you don’t know so you can Rapidly Respond to and mitigate Ransomware, DDoS & other breaches with precision to eliminate the threat and restore operations. Encrypted traffic, and today’s constantly changing application environments, make network security more challenging. CySight stores Big-data in a small footprint that enables unrivaled visibility with a fully Integrated NDR, EDR, XDR, MDR, NTA, DAAS and SIEM with global Geo Analytics, real-time attack maps, and trackback.
SecOps, NetOps, and CloudOps can rapidly determine the origin and causes for changed behavior of the network, network-connected assets, servers, and groups in any size network on Premise and/or in the Cloud. CySight’s Agentless Machine Learning, Predictive A.I. Baselining and Diagnostics, Threat Intelligence, and Micro-Segmentation with integrated Triaging minimize Mean Time to discover and mitigate Cyber and Network risks. Deep Telemetry and Smart metadata allow fine-grained detection, mitigation, accounting, zero-trust monitoring, trackback, and lawful intercept.
CySight’s AI-Driven integrated XDR + NDR + EDR, enables advanced Deep Packet Intelligence and unrivaled visibility into encrypted communication without packet decoding. It surpasses Deep Packet Inspection (DPI), NDR, and Flow Analyzers by more than 20x visibility.
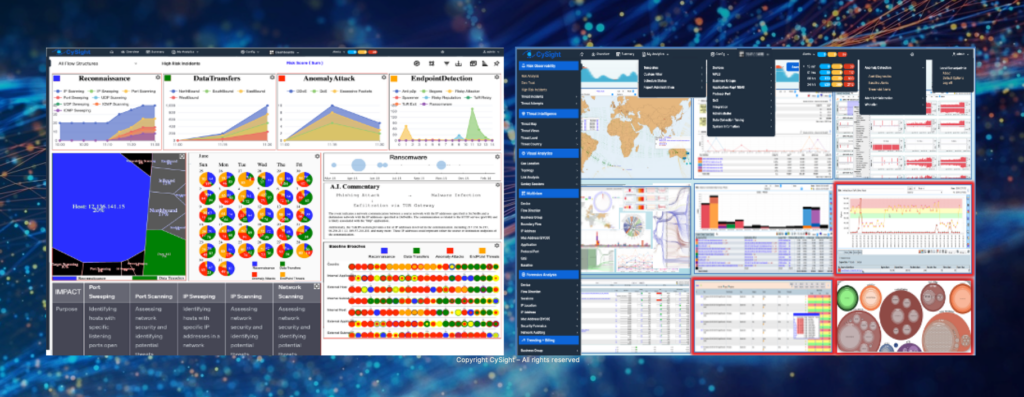
CySight is an extended network detection and response system with predictive artificial intelligence baselining and analytics that delivers scalable, comprehensive, on-demand, and actionable intelligence about everything that crosses your network. Big-data global threat intelligence coupled with machine learning, anomaly detection, and automated diagnostics makes use of cost-effective granular flow-based analytics, dramatically decreasing network security and management costs. Run as a stand alone Probe or process Flow protocols; Router, Switch, Firewall, WiFi, Packet Broker, SDN, Cloud, Kubernetes, Kafka, Netflow, IPFIX, sFlow, ixFlow, VeloCloud, AWS, and other extended flow information may be audited completely using CySight. CySight supports the broadest range of vendors, including KeySight (Ixia), Gigamon, Cisco, Check Point, AWS, and others.
Unique Applications intelligence enables high level awareness dramatically improving network and cloud analytics context and speed to detect and repair. Machine learning and A.I. identify hidden network applications, mitigate network security threats from rogue applications, and reduce network outages.
Eliminates network blindspots with granular insight and transparency of every transaction even when traffic is encrypted enabling security and network issues to be quickly identified. CySight is the only tool that can provide this critical visibility.
Massively scalable allowing clustered query across multiple CySight data-warehouses. Uniquely supports both collection and retention of millions of flows per second. Enables organizations of all sizes to monitor at various levels of granularity from simple visibility to full compliance.
Flexible data mining and reporting from unique 'small-footprint, big data' enables complete forensics. High-granularity retention substantially reduces risk discovering ransomware, malware, p2p abuse and data leakage.
A.I. Diagnostics detects any activity that deviates from normal baselines. Discovers Outliers using dynamic Machine-learning algorithms to provide early warning on DDoS, Anomalous traffic, Advanced Persistent Threats and Insider Threats, securing network, cloud, IoT, and endpoints without packet decryption.
Machine Learning assesses what’s normal and continually monitors and benchmarks identifying problems with speed and finding outliers and detecting vulnerabilities and other network problems. Granular historical baseline analytics enable deep profiling of any aspect of network communications.
Visual Analytics enables you to gain speedy insights into complex data. Visual analytics tools and techniques create an interactive view of data that reveals the patterns within it, enabling everyone to become researchers and analysts.
Logical Network Micro-Segmentation simplifies Zero Trust, Route and Peering analytics and Usage based billing for ISP, MSP, Government, Campus and Enterprises. Segment and measure bandwidth usage of IP groups such as departments or customers and identify location of alerts and security policy breaches.
Leverages economical flow-based analytics from readily available cloud and on-prem networking equipment. Provides a consistent user and feature experience across all network and cloud devices by employing the same management user interface substantially reducing costs to secure and manage a network.
Multi-Focal Deep tech makes full use of granular flow visibility. It can be scaled up or down to suit your network and cloud architecture and used with the broadest flow capable devices in the market – that’s what makes CySight a professional’s choice!
CySight Predictive AI Baselining, NDR, XDR, EDR, Forensics, and Dropless Collection detects dynamic cyber threats (DDoS, DoS), end-point threats (Ransomware), insider threats, and unusual network asset behaviors that other solutions miss by leveraging granular big data, machine learning, artificial intelligence, and end-point threat correlation to establish multi-focal micro and macro baselines of every network and cloud connected asset and communication even when encrypted.

Provides integrated Cyber Security and Event management with comprehensive Intrusion Detection (IDS), Extended Detection and Response (XDR), Endpoint Detection (EDR) and Response (NDR), and security and information event management (SIEM) solution as it gathers, analyzes and presents granular information from multiple network and security devices with comprehensive log auditing, review and incident response. Supports both Real-time and Trending analysis of Usage, Packets, Conversations and 95th percentiles for network behavior anomaly detection, security forensics, capacity planning and billing purposes.

With the increasing abstraction of IT services beyond the traditional server room computing environments have

Why would you need Granular Network Intelligence? “Advanced targeted attacks are set to render prevention-centric

Last week we presented CySight at CyberTech 2016 in Tel Aviv, Israel. Cybertech is the
IT has steadily evolved from a service and operational delivery mechanism to a strategic business
